Our holistic and agile approach to Cybersecurity evolves alongside the ever-changing landscape to continually protect your critical data.
Our Cybersecurity services
After extensive research and collaboration with leading international Cybersecurity vendors, our security team created a range of solutions based on global best practices for small, medium and enterprise organisations. Our comprehensive experience with real-world Cybersecurity incidents has also helped shape each one of our service offerings.
These security services provide an end-to-end holistic solution that protects your critical data through our multi-layered approach. This unique approach is tailored to align with your own unique business strategy and mission.
Why we offer Cybersecurity services
InnoKAT has been keeping Australian SME’s secure since 2004. Our innovative solutions enable our customers to operate securely, monitoring critical systems to ensure their data is protected.
Today, businesses are digitally connected to more devices than ever before. Meanwhile, the internet has grown significantly faster and has become a critical part of global business infrastructure. We have also seen the proliferation of cyber threats at an incredible rate to the point where they are now a common reality for all organisations.
or this reason, InnoKAT continues to evolve and develop Cybersecurity solutions to protect our clients from these ever-changing, advanced and emerging threats.
or this reason, InnoKAT continues to evolve and develop Cybersecurity solutions to protect our clients from these ever-changing, advanced and emerging threats.
Our Managed Services options
Identity & Access Security Assessment (IASA)
An Identity and Access Security Assessment (IASA) provides you with a comprehensive review of your Active Directory domain infrastructure, which is the core component of most corporate Windows networks.
The assessment will review your company network shares against Microsoft Information Security and Risk Management (ISRM) standards to determine if they are set up correctly, comply with best practice and, most importantly, give you visibility of who has access to your information.
The IASA will also include a review of your business Access Controls, including the management of your electronic and digital identities.
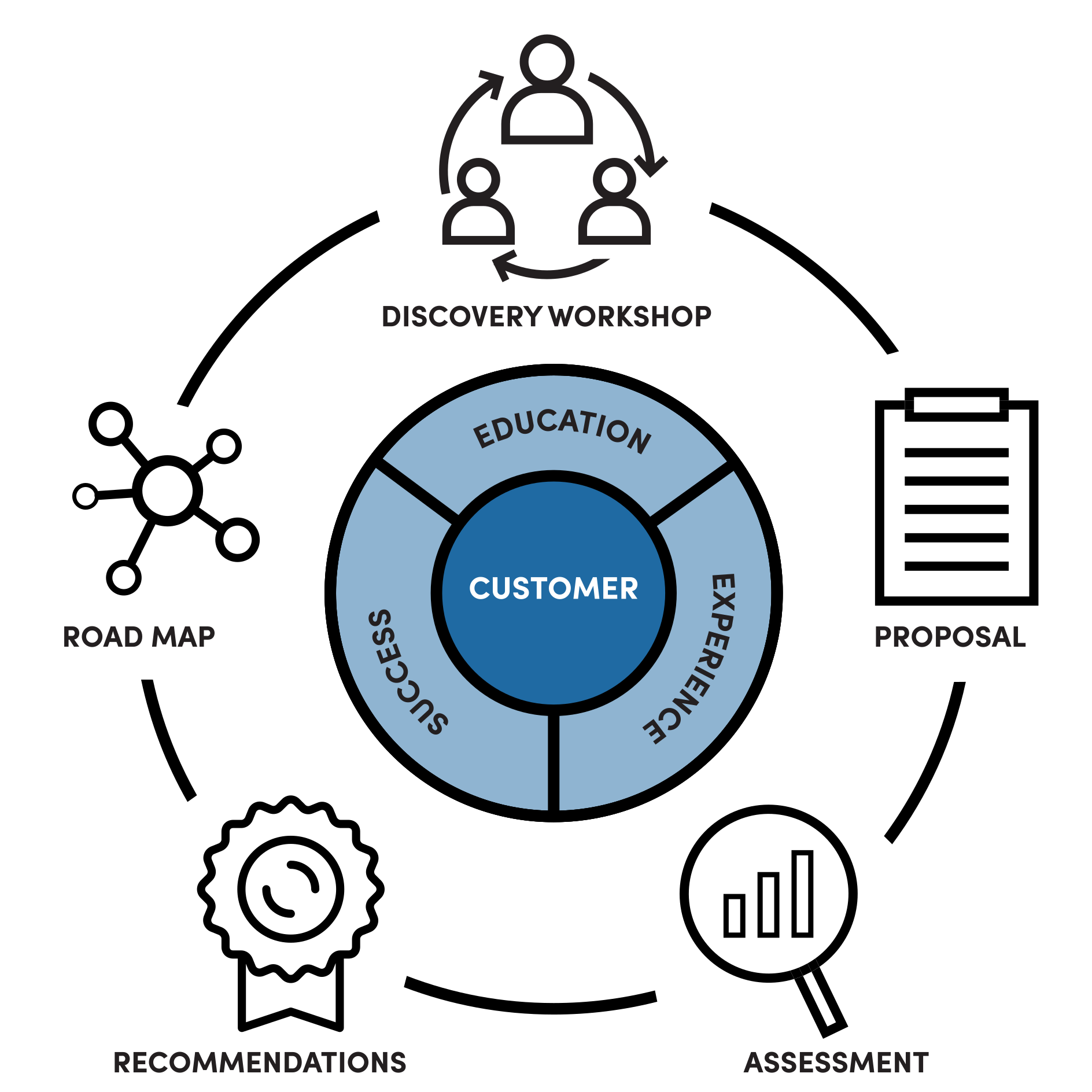
Your Cybersecurity service experience at a glance
We are always looking to help your business grow creating clarity in a complex world. Our Cybersecurity experience focuses on protection and securing the future without hindering user experience.
Cybersecurity Vulnerability Assessment (CVA)
A Vulnerability Assessment is a process of identifying, quantifying and prioritising the vulnerabilities in a system that could give a hacker or an unauthorised user access to your sensitive information.
By conducting this assessment, you can see what aspects of your business systems need to be addressed in order to mitigate risk and maintain a safe and secure technical environment.
The benefits of our Cybersecurity services?
- Clarity
- Local support
- Future safeguarding
- Data-driven decision making
- Collaborative strategyanaged

